In this article:
Creating a NIST CSF Assessment
-
From the bottom left aggregate menu, select the up chevron (1) and create a new NIST CSF 2.0 (CMMI) or NIST CSF 2.0 (FILIPINI) assessment.
-
aggregate menu with up chevron:
-
NIST CSF v2.0 menu options:
If due to screen resolution, the menu does not display those two options, select the CSF Full Assessment and use the model drop-down on the New Assessment modal to select either of the two NIST CSF 2.0 options.
-
New Assessment modal Model drop-options for NIST CSF V2.0:

-
Before starting work on an assessment or performing a risk quantification, Axio recommends adding existing or estimated insurance data to help model the scenarios. Refer to Adding Insurance Data.
Assessment Navigation
Once the new assessment has been created the details need to be entered. The first question in the NIST CSF Full assessment is in the GOVERN (GV) section and the category GV.OC – Organizational Context.
The NIST CSF Assessment has six main functions (1) provided as tabs along the top of the assessment page. Those six functions are navigational also via the left-hand assessment menu, which provides entry points to the assessment categories (2) under each function.
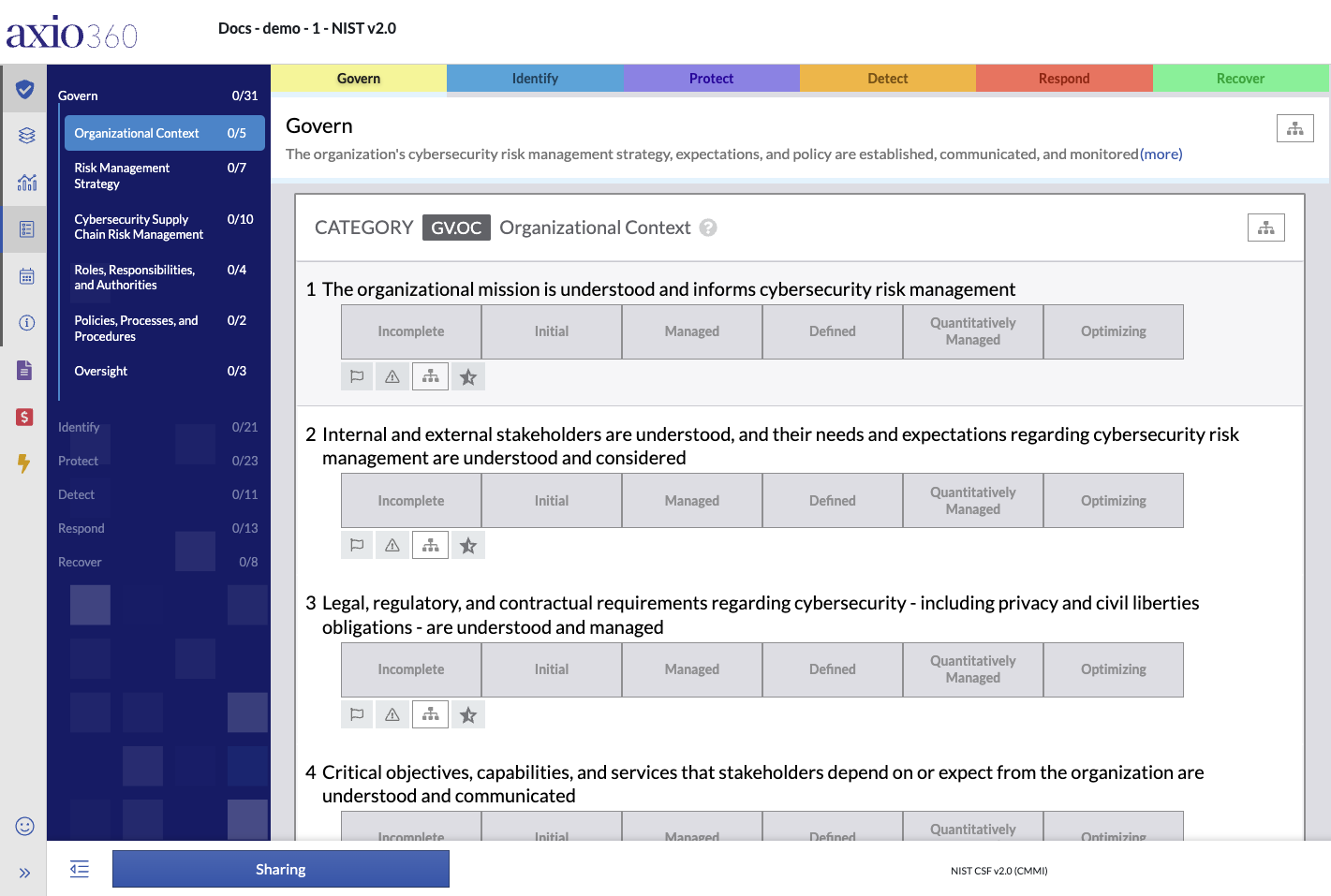
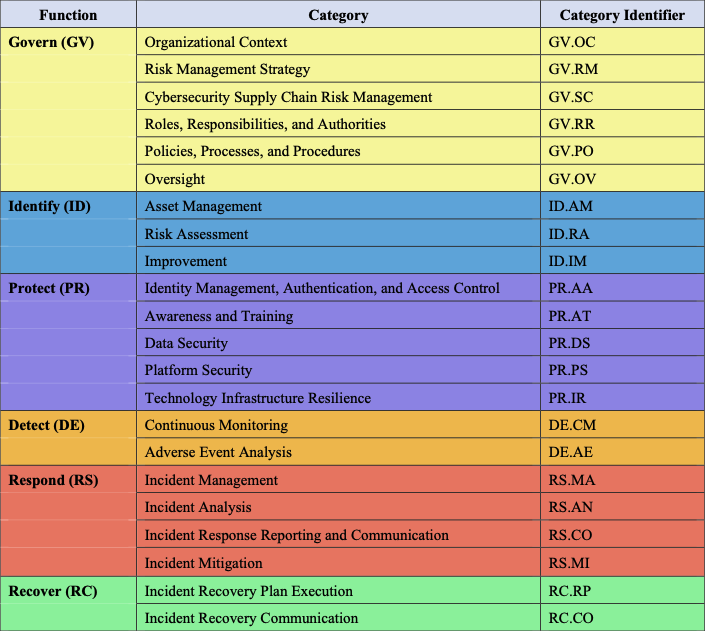
Model Functions and Categories Overview Table
The following image is courtesy of NIST - Cybersecurity Framework.
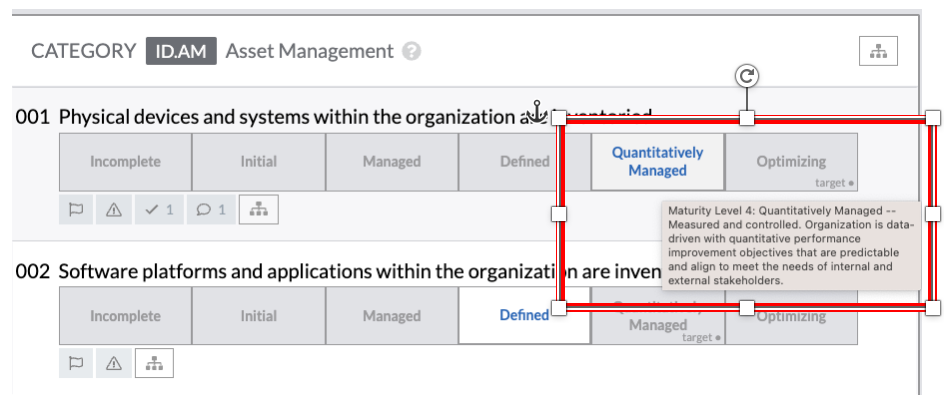
Response Options
The response options are the buttons on the main assessment page that, depending on the assessment are labeled as Incomplete, Initial, Managed, Defined, Quantitatively Managed, Optimizing, Not Implemented, Partially Implemented, Largely Implemented, Fully Implemented, etc.
To respond with either of those options, select the button based on the correct state for your response.
Hover Options
Hovering over the responses displays an explanation of the different response levels available.
Right Navigation Frame
To the right side of an assessment information is provided in 4 tabbed categories, Activity, Evidence, Help, and Advice.
Activity
Provides information about the latest edits/updates to the assessment section, lists action items and contains potential notes.
Under Action items, add any action items relevant to the control or subcategory, such as “Ensure Asset Management Inventory is up to date and add regular cadence to review”. You can assign the Action Item to any user who has access to the assessment and set a date for when the action item should be completed.
For example, for notes, you can type any notes that may be relevant to the response such as “ACME company has an Asset Management program in place. However, it is not regularly reviewed for accuracy and completeness. To save any notes, click Save prior to navigating to another response.
Axio360 can be integrated with ticketing systems, such as ServiceNow’s Service Manager.
Evidence
On this tab, any supporting evidence can be linked to the assessment. Add any evidence related to the response by utilizing Links to Supporting Evidence. You can add the name of your document and link location. Click Save before navigating to another response.
Axio does not store any evidence documents within the Axio360 platform. But external links are supported with various file management platforms, including Microsoft SharePoint, Box.com and Dropbox.
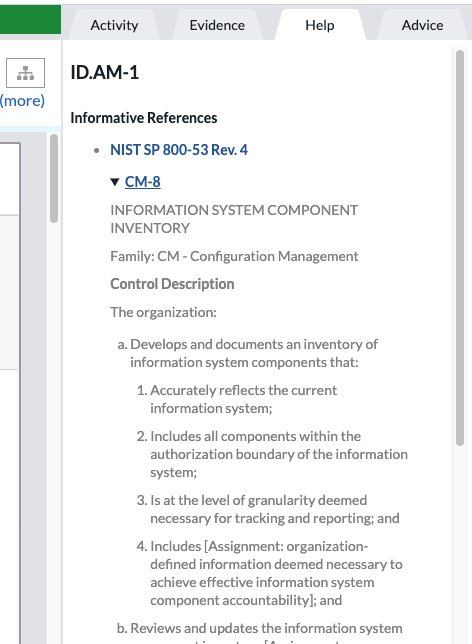
Help
On the Help tab, supporting references are provided. Those are links and references to regulations pertaining to the assessment type. The help is in context to the specific control selected.
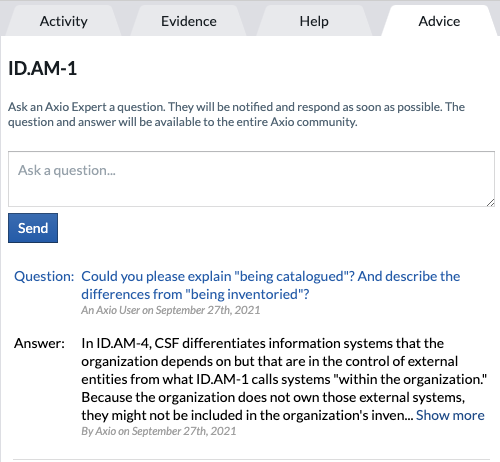
Advice
On the Advise tab, users can ask an Axio Expert a question. The Axio Expert will be notified and respond as soon as possible. The question and answer will be available to the entire Axio community.
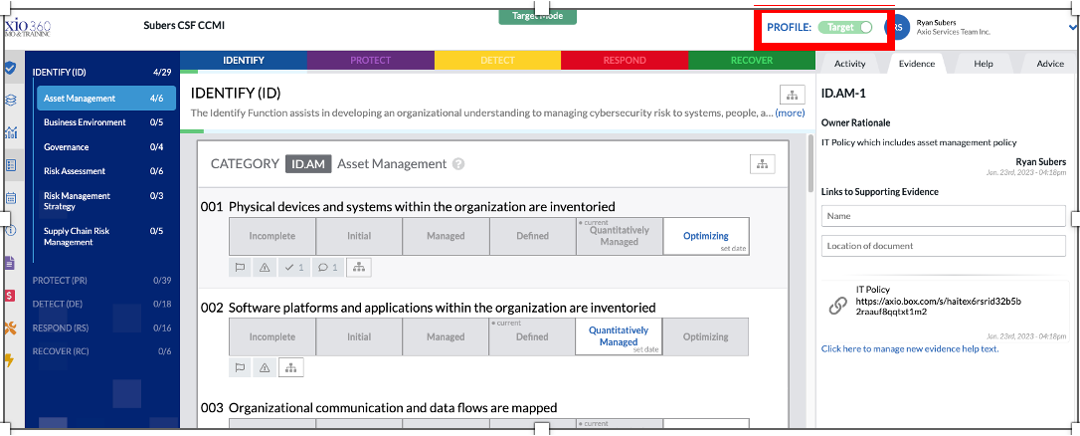
Applying Target Profiles
-
Next to your user avatar find Profile, switch from Current to Target.
Setting the next actions as the targets to achieve over time. To set questions as targets, toggle via “click+shift” when selecting a question.
- Once you are toggled to the Target, select the level you want to set your Target Profile to. Axio recommends setting a target to a level that is attainable within the next year. You can also set specific target dates.
-
Change the Profile back to Current to see targets plus the dates that have been modified for each of the questions.
Generating a Report
After an assessment is complete, you may create a report.
- On the bottom left, click Full Report.
- At the prompt, either select Display notes inline or in an appendix at the end.
-
Click on Generate Report.
Generating a report might take a moment, depending on the data entered.
- When the report is ready, generate a PDF version of the NIST CSF, Axio generated report. You receive a screen notification that the Report generation is complete.
- Select View to view the report.
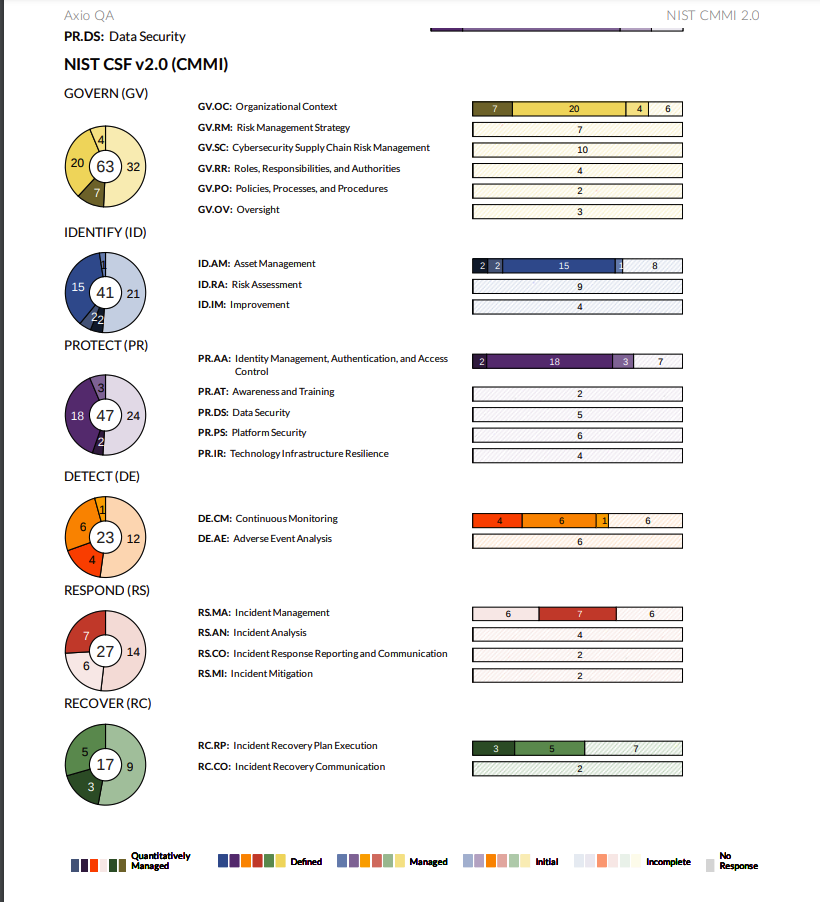
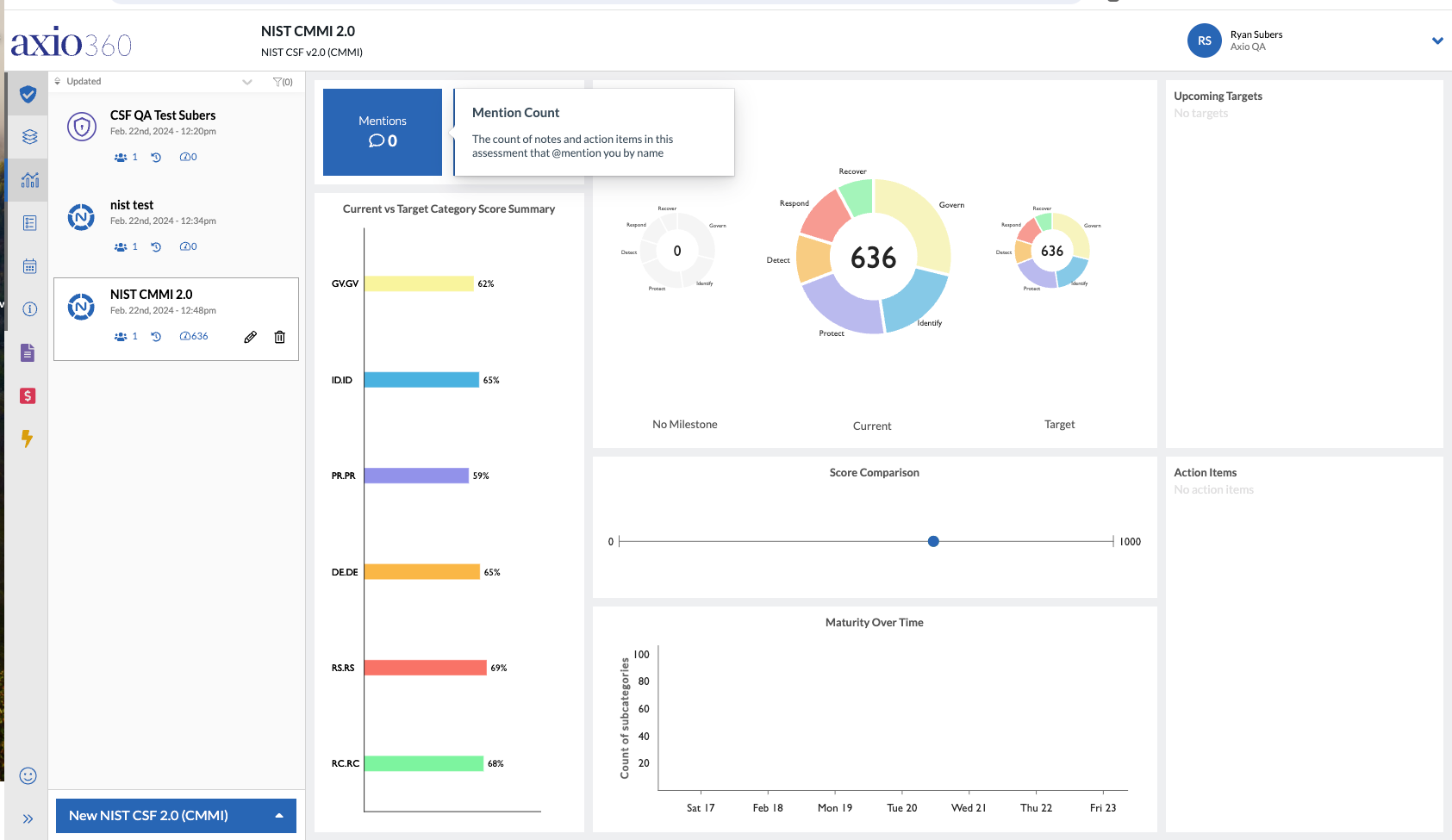
Example NIST CSF v2.0 Dashboard