In this article:
Assessment Exercises
Background
ACME Manufacturing is a computer peripheral manufacturer with an annual income of $0.5B and approximately 7,000 employees. In the past year, they have been impacted by cyber security attacks, which have caused them significant productivity loss and a lawsuit whose results included a mandate that they would have to increase their cyber-security protection and undergo annual audits to prove progress towards a more secure environment, that is in line with their industry peers.
As a result, their Board of Directors and, through them, their Chief Financial Officer (CFO) has instructed their Chief Information Security Officer (CISO) to perform a standardized Security Assessment to understand how secure they are today as compared to other, similarly-sized US-based manufacturing companies. They set goals to reach the higher end of their peer group’s median scores in this assessment and to perform several Cyber Risk Quantification workshops to ensure that their security initiatives (controls) are addressing not only areas of improvement needed based on the assessment findings but also prioritized based on the cost of different cyber security attack vectors that they are susceptible to. In the upcoming hands-on labs, you will perform the tasks requested by the CFO, with a few short detours to review how organizations in other industries, such as Energy, would perform similar actions.
You can use the Axio360 platform to perform these actions as a set of hands-on labs.
Getting Started
Sign in to the Axio360 instance, and start with an Assessment using the NIST CSF Assessment. For our example procedures, we are using Axio’s demo instance.
-
Navigate to https://demo-360.axio.com and sign in. Use your corporate email address. You might have received a temporary password. If not, click Forgot password. An email with a reset link will be sent. If you do not receive that email within 5 minutes, check your Junk Mail folder.
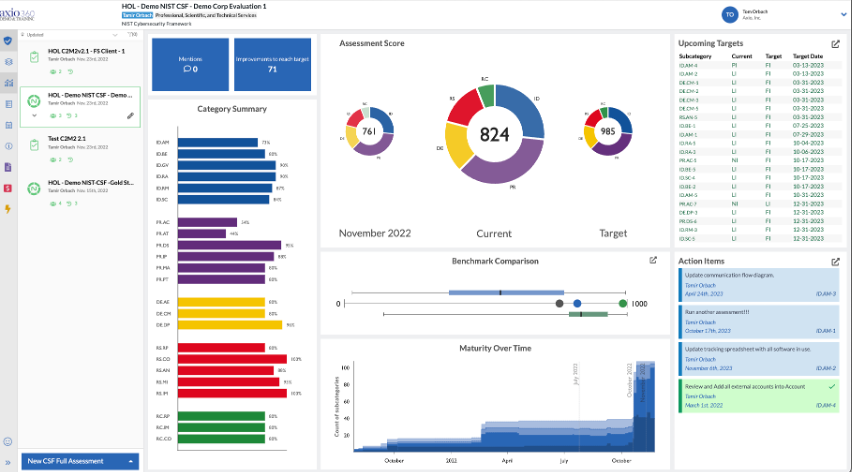
Your landing page will show several sample assessments once you’ve logged in, like the following (the Assessment Scores may vary slightly):
If you do not have any assessments in your instance, you see this on the main portal page:
You can expand and collapse the left navigation menu. Click » to expand and read the full-text menu items. Click « to collapse the menu.
Also refer to Adding Insurance Data, if available, before starting your first assessment.
New Assessment
We will start a new Assessment initially to work through some of the features we just learned about, along with satisfying the requirements of the CFO. The first assessment we will do is on ACME’s IT department.
-
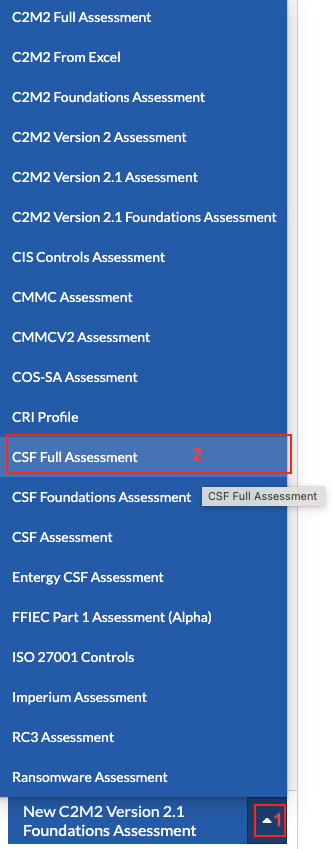
From the bottom left aggregate menu, select the up chevron (1) and create a new CSF Full Assessment (2).
- On the New Assessment modal, enter
- the Assessment Name. For example, use HOL ACME IT Assessment (test).
- a Description. For example, type in All of the organization IT assets.
-
For the Tags, select View Full Tag Tree on the bottom right to see the list of Tags available.
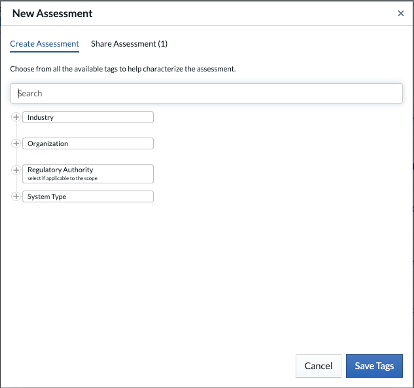
- Expand the Industry node, select Manufacturing.
- Expand the Organization node, select Division or Business Unit or Another Subunit. For this lab, we only assess the IT unit of ACME Manufacturing.
- Exapnd the System Type node, select IT.
- Click Save Tags. Tags can also be added via text entry.
- Ignore the Target Source field for now and click Save.
Working Through an Assessment
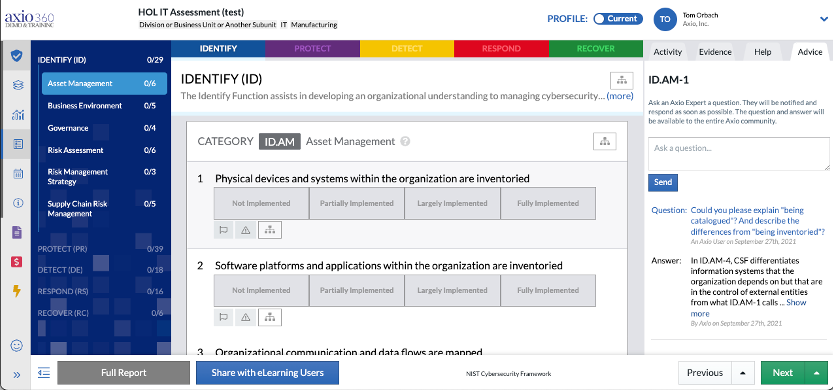
Starting with the current assessment, the first question in the NIST CSF Full assessment is in the IDENTIFY (ID) section and the category ID.AM – Asset Management. It asks explicitly to rank where ACME manufacturing is on Physical devices and systems within the organization are inventoried. Typically this is asked of a group of key stakeholders.
-
While this question is selected, navigate to the right tabbed menu and select Advice.
On the Advice tab, you can ask questions, see questions from other users, or see responses from Axio to questions asked. This type of content might not be there for all questions and categories of an assessment. Customer teams usually create this content with their team interactions and questions for Axio support services members.
-
In the Assessment Management section, hover over Partially Implemented to see inline help Subcategory is implemented with material gaps. Hover over the Largely Implemented to see inline help Subcategory is implemented with gaps that are not material.
A good way to ascertain which answer to select is to hover over each option the first time you answer these questions. Additional information about each question is available in the Advice tab on the top right.
For this example exercise, select Largely Implemented.
Adding Actions, Evidence, and Notes
-
Select the Evidence tab and add the following in Owner Rationale:
ACME Manufacturing’s IT group uses Microsoft’s Endpoint Configuration Manager, a component of which was formerly known as Microsoft Systems Center. This proactively identifies all hardware and software running on IT devices. We have implemented this fully for software but partially for hardware.
- Click Save, to make sure the Owner Rationale is saved.
- Under Links to Supporting Evidence, type ACME Manufacturing IT MS Endpoint Config Mgr. Implementation 02_20_22.
- In the location field, type in SharePoint (if you don’t specify a location, you will not be able to save). In real-world scenarios, you would provide the actual link.
- Click Save.
- Select the Activity Tab and under Target, select Fully Implemented.
- Click the Calendar under target and select a date on a weekday one year from today.
-
Under Action Items, enter the following Enable and enforce hardware inventory in Microsoft’s Endpoint Configuration Manager. Usually, this is assigned to the person responsible for the software or component in question.
In this case, assign it a date corresponding to the date selected for the Target date above. If you don’t see the calendar icon, click in the Action Items text box.
Axio360 integrates with ticketing systems, such as ServiceNow’s Service Manager.
- Under Notes, type in ACME Manufacturing has standardized on Microsoft’s Endpoint Configuration Manager for several functions, including software and hardware inventory. Microsoft’s Endpoint Configuration Manager, including Microsoft’s Configuration Manager, formerly known as Systems Center, Microsoft Intune, Microsoft Desktop Analytics, Microsoft Autopilot, and several other features, will be referred to in several locations in this assessment.
-
Click Save. Very important here to save the edits!
It is usually helpful to have a second person running the workshop to take notes while the first person leads the workshop.
- For the next question, Software platforms and applications within the organization are inventoried hover over Fully Implemented to read the definition and select Fully Implemented.
- Select the Evidence tab to copy and paste the content you added in the previous question, starting with ACME Manufacturing’s IT group uses Microsoft’s Endpoint Configuration Manager….
- Under Links to Supporting Evidence, repeat ACME Manufacturing IT MS Endpoint Config Mgr. Implementation 02_20_21.
Also, refer to our video How to Save Notes and Evidence in Axio360.
Assessment Navigation and Target Profiles
As part of this exercise, we explore how to navigate to other sections of an assessment, and we look at using target profiles.
- To navigate to a question in another section of the NIST CSF Full, in the tree view, or the tabbed top navigation, select PROTECT.
- From the left Identity menu, select Awareness and Training.
-
Next to your user avatar find Profile, switch from Current to Target.
This sets our next actions as the targets we try to achieve over time. Setting questions as targets can also be done by toggling via “click+shift” when selecting a question.
- For each of the five questions, set the Target to Fully Implemented, and use the calendar to set a date to one year from today.
-
Change the Profile back to Current. The targets plus the dates have been modified for each of these questions:
Inheritance or Subcategory Delegation and Flagged Items
Fill in the remaining data points for the exercise as provided below.
- Under Question 1 for All users are informed and trained, select Fully Implemented. The IT group has been proactive about educating IT employees and all ACME Manufacturing employees.
-
This question applies to all of ACME Manufacturing. Click the Delegate Subcategory to Another Assessment button and then select Publish. This will mean that other assessments don’t have to redo the response to this question. The Inheritance inheritance feature shows the question as published/delegated:
Click the Flag.
- Navigate back to the IDENTIFY (ID) function for question 5 under Asset Management Resources (e.g., hardware, devices, data, time, personnel, and software) are prioritized based on their classification, criticality, and business value, click on the Flag.
-
For this question, on Next click the up chevron.
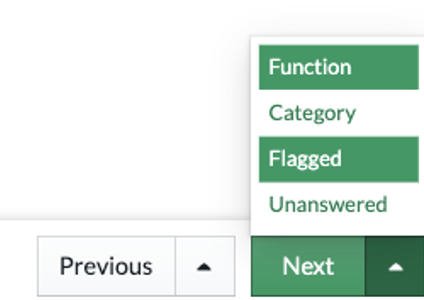
- Select Flagged. This allows you to navigate through all your flagged items.
- Click Next. Clicking Next takes you back to question 1 in the PROTECT (PR) function under Awareness and Training. Using flags this way allows you to flag items you’d like to return to later and quickly navigate through only flagged items.
Assessment Sharing
Now that we’ve made progress on this Assessment, let’s share it with others who can help (or view).
Before sharing a newly created assessment with external users, users outside your domain, save the assessment. Sharing from the Create New Assessment modal works with internal users only.
- Navigate to your user account icon, select Share Assessment.
- On the Ownership and Sharing screen, invite someone from your company who must have the same domain name (please note that it is possible to invite people from other companies, but requires the Admin for your instance to allow external sharing).
- Let the invitee know they may receive an email and ask them to ignore it.
-
Once you have added that person, notice the pencil icon to the right. The default is Edit. You may change it to read-only. For this exercise, keep the default Can edit permission.
-
Under the Invite line, select Add Message and type:
Hi <Employee Name>: Please ignore this invite that would normally be used to allow you to review the assessment and modify it as needed. Thanks - Click Invite.
- Click Done. You have now shared this assessment with the employee as intended.
Generating a Report
While this assessment is incomplete, we will generate a report for this exercise.
- On the bottom left, click Full Report.
- When prompted, select Display notes inline.
- Click on Generate Report.
- Generating a report might take a moment, depending on the data entered. Once the report is ready, select to generate a PDF version of the NIST CSF, Axio report. You will get a screen notification that the Report generation is complete.
- Select View to view the report.
Table of contents
- Report Reviews
- Target Profiles
- Continuous Assessments
- Applicability Setting
- User Groups
- Inheritance - Inheritance or Subcategory Delegation with Flagged Items
- Insurance Data
- Kanban Board