In this article:
Setting up a Scenario Collection
Participants
- Project Lead (or Facilitator, as appropriate)
Timeframe
Start these activities at least one week before the Cyber Risk Quantification Workshop.
Background
A Scenario Collection is a group or bundle of related risk scenarios. Typically, the scenarios within a collection represent the defined collection scope (Scope is explained below). Scenarios within a specific collection can be analyzed individually or together.
Scenario Collections are a key component in the Axio360 Platform. Several activities and capabilities are done at the collection level, including:
- Sharing and collaboration between different people within the organization
- Defining global estimated values that are true for every scenario within a collection
- Defining the functions (e.g., business units, functional areas, components) that are covered by the scope
- Defining the threat objectives (i.e., what the threat seeks to achieve) for the scope
- Aggregating scenario results
- Creating Control Initiatives that apply to some or all scenarios within a collection
- Providing the connection points between insurance analysis and assessment
Activities
Scope the Scenario Collection
Scoping is a critical activity in understanding and defining what the Scenario Collection is to represent or what issue you are trying to understand.
Defining, documenting, and understanding the scope will guide the brainstorming process, as the scenarios considered should be a cross-section of the types of risk that are relevant to the scope considered. Since the potential that an attack could be realized in the next year is set at the collection level, all scenarios in scope will share that common range. However, they are differentiated from each other by their relative susceptibility. (This range is set in a later activity.)
The entire organization is a common initial scope. The scenarios brainstormed and identified for this initial collection should be a cross-section of cyber risks that could impact the organization. However, if the organization is very large, this scope may be too broad.
However, limiting the scope of a collection can help understand how specific risks might affect the organization. Some examples of a limited scope may include the following:
- Specific portions of the organization (e.g., the enterprise, manufacturing, Foreign Offices)
- Business functions or units (e.g., Customer Relations, Human Relations)
- Known threats or attack types (e.g., Insider threat, ransomware)
- Specific vulnerability types (e.g., out-of-support software, insufficient or ineffective security controls)
- Key physical, infrastructure, and/or information assets (e.g., primary customer database, remote working environment, plant)
- Specific projects, such as prioritizing and planning improvements (e.g., proposed purchase of XDR, firewall improvements)
Define the Functions and Threat Objectives
There are two sets of attributes available to a Scenario Collection:
- Functions
- Threat Objectives
Both attributes can be assigned to a scenario to classify it according to the function and threat objective it applies to.
The Functions attribute comprises a user-defined tag set that decomposes a collection scope into smaller units. For example, a Scenario Collection scoped to Human Resources might include Payroll, Recruitment, Benefits, and Training functions.
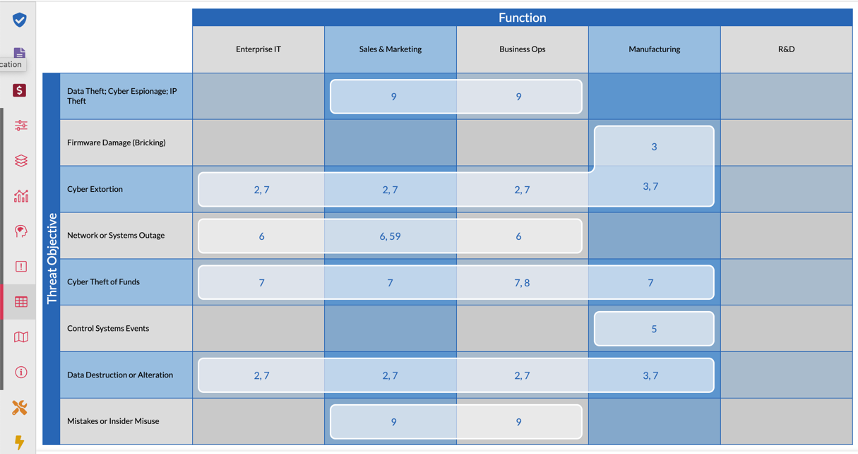
Similarly, the Threat Objectives attribute defines a set of potential impacts and vectors that can be associated with a scenario. Axio provides a predefined set of Threat Objectives (e.g., Data Destruction or Alteration, Network or System Outage) but allows users to add unique objectives.
When used together, the Functions and Threat Objectives attributes appear in the Scenario Coverage Table on the Axio360 Platform. In this table, the intersection between a Function and a Threat Objective identifies one or more scenarios tagged with these attributes. A blank intersection indicates that no identified scenarios contain these unique attributes. The visual nature of the table allows users to inspect where scenarios may be missing.
Enter the “Percent Chance of Attack per Year”
The “Percent Chance of Attack per Year” is a range consisting of minimum to maximum percentages that one of the scenarios in the collection will be realized in the next year. These values can be determined by internal subject matter experts (e.g., risk professionals, threat analysts), industry data, or other sources. It is important to make sure the range reflects the chance that a risk of the defined scope will occur, not necessarily the chance that a specific scenario will occur.
Please note that this range can be estimated during the quantification workshop.
Document the Scenario Collection
Thorough documentation of a Scenario Collection is crucial for recording purposes. Still, it also helps others in your organization to view and understand the scenario details, including scope, assumptions, and the logic behind key decisions.
When documenting a Scenario Collection, it is important to capture the following:
-
Purpose of the collection (What risk questions are we seeking to answer, or what uncertainty are we trying to reduce?)
-
Physical and/or logical boundaries of the scope (To what parts or functions of the organization does this collection apply, or to what type of questions or problems does this apply?)
-
Functions that are contained within the scope (What smaller functions or divisions exist within the scope?)
-
Threat objectives contained within the scope (What are the key things of value to threat actors, and what impacts need to be considered in this scope?)
-
Key assumptions that are true for the collection (What facts are we assuming are valid for all the scenarios within a collection?)
The process for creating notional scenarios to add to a Scenario Collection is included in Creating Notional Scenarios.
Link Assessments and/or Insurance Reviews
Insurance Reviews and Assessments performed in the Axio360 Platform can be directly linked to a Scenario Collection. Linked assessments can be used to calculate scenario susceptibility or influence impacts. As assessments are revised over time, linked scenarios will automatically update to recalculate the quantified risk. Similarly, linked Insurance Reviews allow for impacts in quantified scenarios to be compared to the terms of relevant insurance policies, revealing any potential gaps in type or amount of coverage.
Scenario Collection Examples
This section provides two examples of Scenario Collections, with the collection name, description, and lists of the collection’s Functions and Threat Objectives.
Human Resources Risks
Collection Name: Human Resources Risk Collection-March 2022
Description: This collection focuses on a cross-section of risks to the Human Resources (HR) department. In scope are all applications and data used in the various HR processes. All employee data and personal health information (PHI) fall into this scope. A portion of data relevant to non-employees, specifically personally identifiable information (PII) of job applicants, is also in scope.
This collection seeks to understand the risks to the employee data and HR processes that might be disrupted due to a cyber event. Additionally, we seek to understand if the limitation of liability clauses within HR vendors’ contracts is sufficient to cover potential loss events.
Functions: Recruitment, Benefits, Employee Management
Threat Objectives: Firmware Damage (Bricking), Mistakes or Insider Misuse, Data Destruction or Alteration, Control System Events, Network or System Outage, Data Theft; Cyber Espionage; IP Theft, Cyber Theft of Funds, Cyber Extortion
Percent Chance of Attack per Year: 2% - 6%
Breach Events
Collection Name: Breach of Data (all types)-Enterprise-July 2022
Description: This collection focuses on data breach scenarios across the organization. Breach sizes may vary within this collection but should represent a reasonable and plausible representation of what would happen if a threat actor gained access to the environment and data set. Scenarios should not include availability or integrity concerns.
This collection seeks to understand the risks that may result from the loss of data, including regulated and non-regulated data. A data loss prevention (DLP) solution is being considered, so scenarios should focus on structured and unstructured data to understand to what level a DLP solution could mitigate impacts.
Functions: Employee Data, Customer PII, Research Data, M&A Information, Business Intelligence
Threat Objectives: Firmware Damage (Bricking), Mistakes or Insider Misuse, Data Destruction or Alteration, Control System Events, Network or System Outage, Data Theft; Cyber Espionage; IP Theft, Cyber Theft of Funds, Cyber Extortion
Percent Chance of Attack per Year: 5% - 13%