Axio Glossary
This glossary represents Axio’s interpretration of key terms and descriptions as they pertain to Axio’s product and product use cases.
A
| Term | Description |
|---|---|
| Actor | An actor who knowingly or unknowingly causes harm to a business’ infrastructure. |
| AES | Advanced Encryption Standard |
| Air-gapped | Systems or networks that are disconnected from the internet or insecure networks. |
| anti-malware | Detects and protects against hardware, firmware, or software that is intentionally included or inserted in a system for a harmful purpose. |
| API 1164 | Published by the American Petroleum Institute, API 1164 is a “standard on SCADA security [that] provides guidance to the operators of oil and gas liquids pipeline systems for managing SCADA system integrity and security” [API 2009, pg. iii]. The standard contains some guidance that is applicable to IT as well as OT systems, but it also has detailed guidance that is specific to SCADA systems. The standard is available for purchase from the API website [API 2019]. API does not provide assessment tools or other resources to support implementation of the standard. |
| APT | Advanced Persistent Threats |
| ATP | Advanced Threat Protection |
| Auditor Role | In Axio360 an auditor role can be established by assigning a read-only user role. Auditor roles can be shared. An auditor role is often given to a third-party charged with auditing or reviewing assessment responses or quantification specifications. |
| AV - antivirus | Software designed to detect and destroy computer viruses. |
| Axio | Axio is the leader in SaaS-based cyber management software, which empowers security leaders to build and optimize security programs and quantify risk in financial terms. Axio360 is the only cyber risk management platform to align security leaders, business leaders, and Boards of Directors around a single source of truth about their most critical corporate risks. Since 2013, Axio has been a trusted partner to many of the world’s leading critical infrastructure, energy, manufacturing, and financial services companies, helping drive better visibility and decision-making about cybersecurity priorities and investments. For more information visit www.axio.com. |
| Axio Cyber Risk Quantification Method | Refer to the Cyper Risk Quantification (CRQ) entry. |
B
| Term | Description |
|---|---|
| BCP | Business continuity plan |
| BEC | As in phishing a business email compromise |
| BeEF hooking | Browser exploitation framwork |
C
| Term | Description |
|---|---|
| C2M2 | Cybersecurity Capability Maturity Model (C2M2) was established by the U.S. Department of Energy to improve electricity subsector cybersecurity capabilities and to understand the cybersecurity posture of the energy sector [DOE 2014]. Axio’s David White was the principal architect of C2M2, and a number of other Axions have been involved in its development. C2M2 is widely used by energy sector and other organizations to evaluate, prioritize, and improve cybersecurity capabilities. The model is a common set of 312 industry-vetted cybersecurity practices, grouped into 10 domains, and by objectives within each domain, and arranged according to a maturity level scale of MIL0 through MIL3. An online C2M2 assessment is available on the Axio360 Platform. |
| CERT-RMM | The CERT® Resilience Management Model (CERT-RMM) is a process improvement model for actively controlling and managing operational risk. It encompasses and describes relationships among best practices in cybersecurity, business continuity, and IT operations management. Version 1.1 of the model is available as a book [Caralli 2011]; Version 1.2 is available for free download from the Software Engineering Institute website [Caralli 2016]. Axio’s David White was one of the principal authors of RMM, and a number of other Axions were involved in its development. CERT-RMM is structured into 26 process areas (clusters of related practices) and 565 practices, which are grouped by goals. The practices provide detail in the form of practice descriptions, subpractices, typical work products, and elaborations. CERT-RMM also provides a scheme for incremental improvement using capability levels. |
| CFO | Chief Financial Officer |
| CIA | Triad of information security concerns: Confidentiality, Integrity, and Availability. Also an acronym for Central Intelligence Agency. |
| CIO | Chief Information Officer |
| CIS 18 | Center for Internet Security list of 18 guidelines for security organizations. Refer to Supported Models. |
| CIS Controls | The CIS Controls comprise 6 Basic controls, 10 Foundational controls, and 4 Organizational controls. Each of those contains sub-controls, with a total of 171 sub-controls [CIS 2019]. The controls are further categorized by Security Function: Identify, Detect, Protect, and Respond. The CIS Controls were developed by SANS and are now published by the Center for Internet Security. CIS provides a free method for self-assessment and a number of other resources. |
| CIS CSC | CIS Critical Security Controls |
| CISO | Chief Information Security Officer |
| CISSP | Certified Information Systems Security Professional |
| Continuous Assessment | Establishing an assessment history via Milestones. |
| Control Initiatives | In the Axio CRQ Method, a Control Initiative is one or more administrative, technical, or physical control improvements or risk mitigation actions that could be implemented to reduce susceptibility to, or mitigate the impact of, an identified cyber risk. Control Initiatives can represent a range of activities, refer to Control Initiatives. |
| CRO | Chief Revenue Officer |
| CRQ (Cyber Risk Quantification) | Cyber risk quantification involves the application of risk quantification techniques to an organization’s cybersecurity risk. |
| CSP | Content Security Policy: The name of a HTTP response header that modern browsers use to enhance the security of the document (or web page). Preventing cross-site scripting, clickjacking, and other code injection attempts. |
| CSRF | Cross-site request forgery |
| CTO | Chief Technology Officer |
| CVE | Common Vulnerabilities and Exposures, a list of publicly disclosed vulnerabilities and exposures. |
| CVSS | The Common Vulnerability Scoring System (CVSS) is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat. |
| Cybercrime | Cybercrime is any criminal activity that involves a computer, networked device or a network. |
| Cyber Event | An event that results in unauthorized access to and acquisition of nonpublic information or the disruption or misuse of an information system. |
| Cyber Program Planning and Management | Refer to NIST Computer Security Resource Center |
| Cyber Resilience Optimization | Ongoing and careful selection of proven controls (including cyber insurance) that improve an organization’s ability to adapt to, prepare for, respond to, and recover from cyber risks that affect its core operational capabilities. |
| Cyber Risk | The potential for harm or loss related to the use of or dependence on digital assets. |
| Cyber Risk Condition Coverage | The percentage of conditions within decision expressions that have been evaluated to both true and false. Note that 100% condition coverage does not guarantee 100% decision coverage. Refer to NIST Computer Security Resource Center |
| Cyber Risk Consequences | The magnitude of harm that can be expected to result from the consequences of unauthorized disclosure of information, unauthorized modification of information, unauthorized destruction of information, or loss of information or information system availability. Sources: NIST SP 800-34 Rev. |
| Cyber Risk Curve | Axio’s Cyber Risk Curve illustrates cyber risk reduction based on an investment perspective. Initial investments should be in cyber capability development—controlsto protect and sustain. As the risk curve flattens, cyber insurance becomes an efficient means to further reduce risk. Harmonizing the investment in technological and financial controls requires better exposure and loss metrics.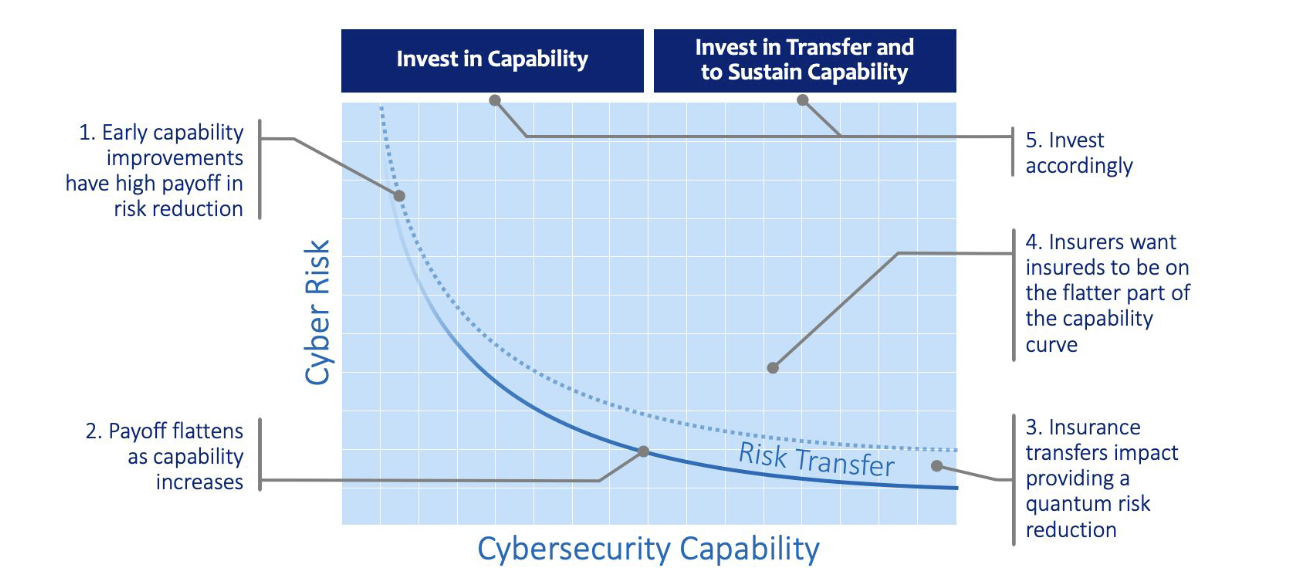 |
| Cybersecurity | The state of being protected against the criminal or unauthorized use of electronic data, or the measures taken to achieve this. Cybersecurity can be categorized into: * Critical infrastructure security * Application security * Network security * Cloud security * Internet of Things (IoT) security. |
| Cybersecurity duty of care | Understanding one’s cyber risk, maintaining a mature cybersecurity program, having the financial ability to recover from an event, and being able to prove all of that with data. (Axio, of course, enables all.) |
| Cyberthreat | Probability that a specific type of attack may occur. The possibility of a malicious attempt to damage or disrupt a computer network or system. |
D
| Term | Description |
|---|---|
| Defense in Depth | Four layers security model. L1: Perimeter Defense; L2: Host Protection; L3: Operation System and Application Protection; L4: Data/Information Protection |
| Delegation | Practice responses in Axio360 can be delegated from one completed assessment to another. |
| DevSecOps | Security practices integrated DevOps approach. |
| DES | Data Encryption Standard |
| Dictionary-based attack | Automated password guessing attack |
| DREAD | DREAD was part of a system for risk-assessing computer security threats that was formerly used at Microsoft and disconntinued in 2008. |
E
| Term | Description |
|---|---|
| Elaborated Scenario | Details that give a deeper understanding of the users and users’ characteristics that may help with assessments. |
| ERM | Enterprise Risk Management |
| Evidence Warehousing | Evidence Warehousing refers to Axio360’s feature allowing users to link to supporting documents and other artifacts. |
| Exposure | The condition of being subject to or in contact with a potential event that could cause a harm to the organization. |
F
| Term | Description |
|---|---|
| FAIR | Factor Analysis of Information Risk (FAIR) FAIR provides a model for understanding, analyzing and quantifying information risk in financial terms. A standard taxonomy and ontology for information and operational risk. It includes a framework for establishing data collection criteria, measurement scales for risk factors, a modeling construct for analyzing complex risk scenarios, and integration into computational engines such as RiskLens for calculating risk. It is the only international standard Value at Risk (VaR) model for cybersecurity and operational risk. FAIR Institute |
| FI | Fully implemented, term used in Aggregates Dashboard. The practice is implemented and operating as intended, and substantially covers in-scope assets. The practice is monitored and updated as needed. |
| First-party Financial Impact | Expenses an organization incurs as a direct result of a cyber event. |
| First-party Tangible Impact | Property and environmental damage experienced by an organization resulting from a cyber event and bodily injuries to its employees resulting from the event. |
| Forced-ranking Process | A system that ranks risks based on presumed severity/impact. |
| FQN | Fully Qualified Name, used in Practice FQN, maps different data sets during assessment import and export procedures. They are formed based on abbreviated Domain, Category, and Practice references. Not to be confused with FQDN (Fully Qualified Domain Name). |
G
| Term | Description |
|---|---|
| GLBA compliance | The Gramm-Leach-Billey Act of 1999 is a standard of security for financial institutions. |
| GQIM | The Goal-Question-Indicator-Metric (GQIM) Method, provides a way to derive meaningful metrics that directly support the achievement of business objectives. The method is typically conducted in a workshop setting and has five steps: (1) identify business objectives that establish the need for resilience and cybersecurity; (2) develop one or more goals for each objective; (3) develop one or more questions that, when answered, help determine the extent to which the goal is met; (4) identify one or more pieces of information that are required to answer each question; (5) identify one or more metrics that will use selected indicators to answer the question Stewart 2015. |
H
| Term | Description |
|---|---|
| HIPAA | The Health Insurance Portability and Accountability Act |
I
| Term | Description |
|---|---|
| ICS | Guide to Industrial Control Systems (ICS) Security, NIST Special Publication 800-82 SP 800-82 is published by the U.S. National Institute of Standards and Technology (NIST). It “provides guidance for establishing secure industrial control systems (ICS). These ICS, which include supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS), and other control system configurations such as Programmable Logic Controllers (PLC) are often found in the industrial control sectors” [NIST 800-82 2015, pg. 1]. “The document provides a notional overview of ICS, reviews typical system topologies and architectures, identifies known threats and vulnerabilities to these systems, and provides recommended security countermeasures to mitigate the associated risks. Additionally, it presents an ICS-tailored security control overlay, based on NIST SP 800-53 Rev. 4 [22], to provide a customization of controls as they apply to the unique characteristics of the ICS domain” [NIST 800-82 2015, pg. 1-1]. |
| IDIQ | Indefinite delivery/indefinite quantity contract model |
| Axio Impact Descriptions | Refer to Quadrant Help Texts |
| Inheritance | In Axio360 responses to assessment practices can be inherited from other assessments. Also refer to the Delegation entry. |
| Insurance Stress Testing | A service in which Axio analyzes selected policies in the client’s insurance portfolio to discover how they are worded with respect to a cyber peril, whether there is explicit cyber coverage, whether cyber is explicitly excluded, or whether the policy is silent regarding cyber. |
| Institutionalization | Incorporation into the ingrained way of doing business that an organization follows routinely as part of its corporate culture. (RMM) |
| IPS | Intrusion Protection System |
| ISO/IEC 27001 | ISO/IEC 27001:2013 Information technology — Security techniques — Information security management systems — Requirements ISO 27001 or ISO/IEC 27001, as this is commonly called (IEC is the International Electrotechnical Commission), is an international information security standard that provides “requirements for establishing, implementing, maintaining and continually improving an information security management system.” “This International Standard can be used by internal and external parties to assess the organization’s ability to meet the organization’s own information security requirements” [ISO/IEC 2013]. It must be purchased from ISO. |
K
| Term | Description |
|---|---|
| KMaas | Key Management as a service |
| KMS | Key Management System |
| KRACK | WiFi-based vulnerability |
L
| Term | Description |
|---|---|
| LI | Largely implemented, term used in Aggregates Dashboard. The practice is implemented and operating as intended but may not substantially cover in-scope assets. There are recognized opportunities for improvement. |
M
| Term | Description |
|---|---|
| malware | Malicious software. A catch-all term for anything that could be called malicious including CryptoLockers, spyware, viruses, worms, trojans, and backdoors. |
| MFA (Multi-factor Authentication) | An authentication system that requires more than one distinct authentication factor for successful authentication. Refer to NIST Computer Security Resources. |
| Means | An actor having the financial or technical bandwidth to target and harm a business with an attack on their infrastructure. |
| MIL | Maturity Indicator Level, which can span from 0-3 in a report. |
| Mitigate | Lessen the severity of a cyber attack |
| Motive | Opportunity and motivation to target and harm a business. |
N
| Term | Description |
|---|---|
| Netblock | Range of IP Addresses |
| Net Neutrality | Net neutrality is the principle that an internet service provider (ISP) has to provide access to all sites, content and applications at the same speed, under the same conditions without blocking or giving preference to any content. |
| NI | Not implemented, term used in Aggregates Dashboard. The practice is not implemented and/or the practice is not functional (i.e., it has been implemented but is not active.) |
| NIST CSF | The Framework for Improving Critical Infrastructure Cybersecurity (as this is actually titled), a.k.a. the Cybersecurity Framework, is published by the U.S. National Institute of Standards and Technology (NIST). The core of the Framework is a set of desired activities and outcomes organized into 5 Functions, 23 Categories, and 108 Subcategories (practices). Each Subcategory is accompanied by Informative References across multiple standards, such as NIST 800-53 and ISO/IEC 27001. The Framework also includes Implementation Tiers, which “help determine the extent to which cybersecurity risk management is informed by business needs and is integrated into an organization’s overall risk management practices” [NIST CSF 2018, pg. 8]. CSF has gained widespread use, and many assessment tools, implementation guidance, and other supporting resources are provided for it by other organizations. An online CSF assessment is available on the Axio360 Platform. |
| NIST Special Publication 800-171 | NIST SP 800-171 provides a set of recommended security requirements for protecting the confidentiality of U.S. federal government controlled unclassified information (CUI) when it is resident in nonfederal systems and organizations [NIST 800-171 2016]. The requirements are intended for use by federal agencies in contractual vehicles or other agreements established between those agencies and nonfederal organizations. Security and Privacy Controls for Information Systems and Organizations, NIST Special Publication 800-53 (NIST 800-53) NIST SP 800-53 (or NIST 800-53), as this is commonly called, is a comprehensive, detailed catalog of technical and nontechnical security and privacy controls. Revision 4 was published in 2013 [NIST 800-53 2013], a draft of revision 5 was published in August 2017 [NIST 800-53 2017], and another Revision 5 draft is planned for release in the spring of 2019. Although SP 800-53 was developed by the U.S. National Institute of Standards and Technology originally for use in the U.S. federal government, it has gained widespread use globally by all kinds of organizations. NIST SP 800-53 Revision 5 contains more than 1,500 controls organized into 20 families. Each control contains a control description, supplemental guidance, control enhancements and references (if applicable), and the priority and baseline allocation for the control and its enhancements. In addition to the control catalog, SP 800-53 provides guidance about risk management, security control specification and selection, and baseline security controls for low-impact, moderate-impact, and high-impact information systems. |
| Notional Scenario | A scenario existing only in theory or as a suggestion or idea. |
O
| Term | Description |
|---|---|
| OCTAVE® | The Operationally Critical Threat, Asset, and Vulnerability EvaluationSM (OCTAVE®) [SEI 2008] is a methodology for assessing information security risk. It is published by the Software Engineering Institute. The OCTAVE approach is driven by operational risk and security practices. It enables organizations to make information-protection decisions based on risks to the confidentiality, integrity, and availability of critical information-related assets. All aspects of risk (assets, threats, vulnerabilities, and organizational impact) are factored into decision making. OCTAVE-S is a variation of the approach tailored to the limited means and unique constraints typically found in small organizations (less than 100 people). OCTAVE Allegro is another variation of the approach that allows broad assessment of an operational risk environment without the need for extensive risk assessment knowledge. It focuses primarily on information assets in the context of how they are used, where they are stored, transported, and processed, and how they are exposed to threats, vulnerabilities, and disruptions as a result. Axion Lisa Young was involved in the development and application of OCTAVE. |
| OpenID | Authentication protocol |
| Operational Focus | An operations-focused company develops a culture focused on systems, procedures, and the bottom line. |
| OWASP | An Open Web Application Security Project curated list of the top 10 threats in information security. |
P
| Term | Description |
|---|---|
| PaaS | Platform as a service |
| PAM (Privilege Access Management) | Privileged access management (PAM) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized privileged access to critical resources. |
| Percent Chance of Attack per Year | A range consisting of minimum to maximum percentages of risk that one of the threat scenarios will be realized in the next year. These values can be determined by internal subject matter experts (e.g., risk professionals, threat analysts), industry data, or other sources. It is important to make sure the range reflects the chance that a risk of the defined scope will occur, not necessarily the chance that a specific scenario will occur. |
| PHI | Protected Health Information |
| PI | Partially implemented, term used in Aggregates Dashboard. The implementation of the practice is incomplete, the practice is not operating as intended, and/or the practice does not substantially cover in-scope assets. There is a substantial opportunity for improvement. |
| PII | Personal Identifiable Information |
| Principle of least privilege | The concept that users should have only enough permissions as necessary for threir role in a system. |
R
| Term | Description |
|---|---|
| Ransomware | A type of malicious software designed to block access to a computer system until a sum of money is paid. |
| Reduce | Lower the likelyhood of an cyber attack |
| Resilience | An organization’s ability to adapt to, prepare for, respond to, and recover from a cyber risk that affects its core operational capabilities. |
| Risk Heat Map | Axio UI term. A Risk Heat Map visualizes the areas that are most vulnerable to an attack based on provided assessment data. It can also visualize areas, teams, or departments that are behind schedule in their assessment. |
S
| Term | Description |
|---|---|
| Safelist | List of allowed programs to install and run on a system |
| Scenario Collection | A Scenario Collection is a group or bundle of related risk scenarios. Typically, the scenarios within a collection are representative of the defined collection scope (Scope is explained below). Scenarios within a specific collection can be analyzed individually or together. Refer to Setting up a Scenario Collection. |
| Scenario Dashboard | Refer to Simulate the impact of Control Initiatives on risk mitigation |
| Slug | User-friendly URL |
| Susceptibility | The probability that an event, once initiated or attempted, will succeed and lead to the realization of the scenario describing the event. Susceptibility is a component of the overall probability of the scenario; susceptibility is the element of probability that the organization has the most control over. |
T
| Term | Description |
|---|---|
| Third-party Financial Impact | Any financial impact that a third party suffers from a cyber event and seeks to recover from an organization (the first party affected), and the organization’s costs associated with adjudicating those demands. |
| Third-party Tangible Impact | Property and environmental damage and bodily injuries to others resulting from a cyber event for which an organization is liable. |
| Threat | A natural or man-made occurrence, individual, entity, or action that has or indicates the potential to harm life, information, operations, the environment, or property. |
| Threat Objectives | Objective of the hacking entity, when they chose to hack an organization. |
| Triple DES (3DES) | Symmetric key block cipher |
| TSA Pipeline Security Guidelines | Published by the U.S. Transportation Security Administration, 2010. These guidelines provide the basis for TSA’s Pipeline Security Program Corporate Security Reviews and Critical Facility Security Reviews, although they are recommendations rather than requirements. “Baseline” and “enhanced” security measures for both physical and cyber security are given. Baseline measures alone are intended for use for non-critical pipeline cyber assets, which as defined by the Guidelines are OT systems that monitor operations on the pipeline. Both baseline and enhanced measures should be used for critical pipeline cyber assets, which as defined by the Guidelines are OT systems that can control operations on the pipeline [TSA 2018]. |
| TTP (Tactics, Techniques, and Procedures) | The behavior of an actor. A tactic is the highest-level description of this behavior, while techniques give a more detailed description of behavior in the context of a tactic, and procedures an even lower-level, highly detailed description in the context of a technique. Refer to NIST Computer Security Resource Center |
V
| Term | Description |
|---|---|
| Value at risk | “Value at risk (VaR) is a statistic that measures and quantifies the level of financial risk within a firm, portfolio or position over a specific time frame. This metric is most commonly used by investment and commercial banks to determine the extent and occurrence ratio of potential losses in their institutional portfolios. Risk managers use VaR to measure and control the level of risk exposure. One can apply VaR calculations to specific positions or whole portfolios or to measure firm-wide risk exposure” [Kenton 2019]. |
| Vulnerability | An exposure, flaw, or weakness that could be exploited by a threat. Also, the susceptibility of an organizational service or asset to disruption. (RMM) |
Z
| Term | Description |
|---|---|
| zero-day | previously undisclosed vulnerability |